Our Mission
At IXI Labs, we’re solving critical problems by redefining how authorisation and secure communications are managed in the digital world. We specialise in creating solutions where cryptography and user sovereignty are at the core.
Over 100M*Messages Encrypted and DeliveredOur solutions are running 24/7 on our decentralised, open-source network. Currently distributed and encrypted across 200+ nodes worldwide.
* Estimate extrapolated from push notification metrics
* Estimate extrapolated from push notification metrics
Over 18.8KUsers Benefiting From IXI SecurityOur solutions, projects and products are loved and trusted by thousands of users globally.
8 yearsof DevelopmentBacked by 20 years of research in the fields of cryptography, distributed networks, highly scalable systems and data structures. With 8 years of active development, we continue to build secure and encrypted solutions for the market needs.
Solving Your Challenges
In today’s digital landscape, the foundation of online identity, security and communication is fundamentally flawed.

WHAT WE SPECIALISE INFullstack Encryption and Distributed Compute
At IXI Labs, we’re solving critical problems of the new digital world by redefining how identity, security and communications are managed. We develop software and firmware solutions where cryptography, maximum availability and user sovereignty are at the core.
 Public Key as IdentityRemoving the need for usernames, third-party trust, or arbitrary identifiers. All metadata (names, IPs, etc.) is linked directly to your public key, ensuring a more reliable and secure identity.
Public Key as IdentityRemoving the need for usernames, third-party trust, or arbitrary identifiers. All metadata (names, IPs, etc.) is linked directly to your public key, ensuring a more reliable and secure identity. Device Self-SovereigntyEach device acts as a self-contained unit. This way your service doesn’t need to rely on internet connectivity or other servers for providing critical functionality to the users.
Device Self-SovereigntyEach device acts as a self-contained unit. This way your service doesn’t need to rely on internet connectivity or other servers for providing critical functionality to the users. Secure Communication ProtocolsOur solutions enable secure device discovery and communications out-of-the-box, while our cryptographic methods ensure that your data remains secure, regardless of the underlying transport layer.
Secure Communication ProtocolsOur solutions enable secure device discovery and communications out-of-the-box, while our cryptographic methods ensure that your data remains secure, regardless of the underlying transport layer.
Let’s find out how we can help you improve your business.
USE CASES
When advanced encryption, scalability and low cost solution is required.
 Access ManagementAccess controls and management. Bridging technologies for a secure environment.
Access ManagementAccess controls and management. Bridging technologies for a secure environment. Device ConnectivityUser-to-user, user-to-device, device-to-device and the secure way to operate in the IoT world.
Device ConnectivityUser-to-user, user-to-device, device-to-device and the secure way to operate in the IoT world. CommunicationsTrustless communication platform keeping our world securely connected for decades to come.
CommunicationsTrustless communication platform keeping our world securely connected for decades to come.
TECHNOLOGY & PRODUCTSOur Latest Projects
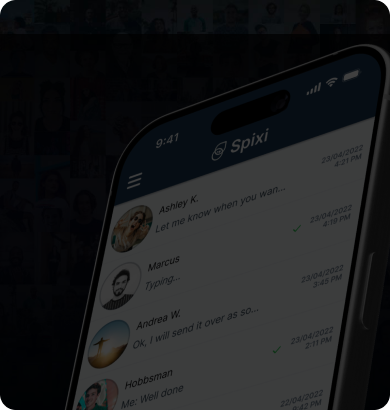
Spixi Private Chat
Spixi is an encrypted peer-to-peer communications app with exclusive features and reduced operational costs.Visit Spixi Website
Ixian Distributed Ledger
Distributed Ledger Technology with a high performing and robust blockchain network.Visit Ixian Website
